
Load Balancing Routers
Load Balancing Routers also referred to as dual-Wan multihoming or routing, and it's the ability to balance all the traffic between two WAN link without having to use any complex routing protocols. In addition, it balances network sessions like email and web over multiple connections, so the amount of bandwidth used by every LAN user spreads. (Load Balancing Routers, 2018)
Proxy Server
A proxy server is a server, that's an intermediary, which handles requests from clients seeking resources from other servers, where a client requests some service, while being connected to the proxy server, the service could be something like a connection, a file and even a web page.
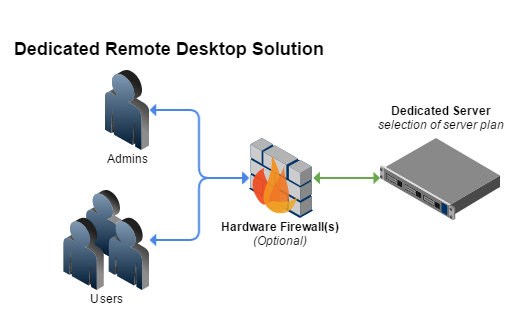
Hardware Firewalls
Hardware Firewalls can be found in broadband routers. In addition, hardware firewalls are important since they can protect the devices on the local network. However, hardware firewalls usually have four network ports minimum. As well as, hardware firewall uses packet filtering to examine the header of a packet, where it determines the source and destination. (Webopedia, 2018)
Content/Traffic Filter
Content/Traffic Filter also known as egress filtering, it's the action of restriction the flow of information from one network to another.
Virtual Private Networks
Virtual Private Networks also known as a (VPN). However, VPN extends the private network across a public network, which then enables users to receive data and send it via public or shared networks, as if those devices are connected to the private network itself. (Web.archive, 2018)
Citrix Services / Terminal Server (Remote Desktop)
Remote Desktop Services also known as "Terminal Services", allows users to control virtual machine over a network or remote computers. However, Remote Desktop computer, is a Microsoft implementation, where an entire desktop computer running on RDS with windows OS.
Routing Tables
Routing tables also known as "routing information base" and abbreviated as (RIB), routing tables is data table stored in a networked computer or a router. All the networked devices that use the TCP/IP protocol have a routing table, the routing table is used to determine, where the packets should be sent to. In addition PC’s won’t be able to communicate with other computers on the same subnet without a routing table.
NAT & PAT
NAT stands for "Network Address Translation", it's a method where one IP address space is remapped, and this is done by modifying network address information in IP header of packets. (SearchNetworking, 2018).
PAT stands for "Port Address Translation" it is an extension to NAT, which is the "Network Address Translation". However, PAT is simply responsible for permitting devices on a LAN, which is the "Local Area Network" to be mapped to the same public IP address. (SearchNetworking, 2018)
VOIP
VOIP stands for "Voice over Internet Protocol" also known as (IP telephony). However, VOIP is a set of technologies that are used for delivering multimedia and voice communications over the IP, which stands for (Internet Protocol). In addition, broadband phone service, internet telephony and broadband telephony refers to the communication services like (voice-messaging, fax, voice and SMS) over the public internet, rather than over a PSTN, which stands for (Public Switched Telephone Network). As well as, this process takes place Instead of the voice signals being transmitted over a circuit-switched network, the digital information is transmitted via as IP packets over a packet-switched network. (VoiceOverIP, 2018)
Firewalls and Traffic Filtering
A firewall provides network security, which means that the firewall monitors incoming and outgoing traffic, where the firewall puts a barrier between a trusted network, which the user is using and an untrusted network like the internet. (Firewalls, 2018)
Traffic Filtering
Traffic filtering is a method used to enhance network security by filtering network traffic based on many types of criteria. (Comptechdoc, 2018)
Port Mirroring
It's the process, where the packets entering a VLAN or the packets entering or exiting a port are copied. However, this is used to monitor the traffic on the network.