
TCP/IP
IP (Internet Protocol Security) also abbreviated as (IPSec). However, IPSec is a network protocol that encrypts and authenticates the packets of data that is sent over a network. In addition, IPsec also includes the protocols to establish mutual authentication between the agents at the beginning of the session and negotiation of cryptographic keys to use during the session. IPSec can also protect the data flows between security gateways and hosts, it uses cryptographic security to protect communications over Internet protocol network. (Technet.microsoft, 2018)
DNS
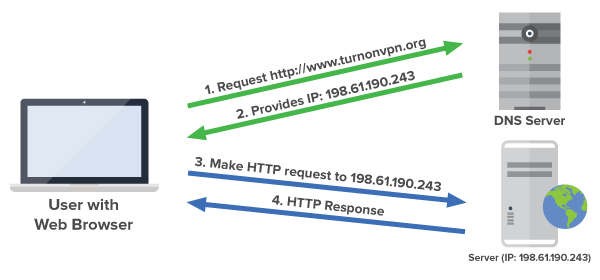
DNS stands for (Domain Name System), it is used to translate the actual domain into the number, which will then open the searched website. However, whenever someone visits a website, if someone is visiting www.google.com there is an extra dot added at the end that the user doesn"t see, this dot represents the root. In addition, whenever a search is taking place the operating system and the browser, will try and see if they know what the IP address is, this IP address might be in the memory or configured on the device you're using. The memory is known as cache. Hence, if the operating system and the browser both does not know, then the operating system will ask the resolving name system. As a result, the resolving name system does not actually know what the IP address is, but it does know where it can be found, which is in the TLD com, TLD stands for (Top Level Domain). To point out, the TLD doesn't know either but it does know where the servers can be found. The domain's registrar helps the Com TLD name servers to know which authoritative name servers to use. The registrar knows which authoritative name servers to use. Then, the authoritative name servers tells the browser what IP address it has to go to.
Name Servers
NameServers control which server your domain goes to. If the domain name is searched in the browser then the info is sent to the registrar, for example GoDaddy.com. However, GoDaddy will now send the visitor to the website, they are looking for, which is an easy process, since the hosting service is linked with your domain. However, this is what a NameServer does it links your Registrar to the hosting service provider. In addition, NameServers can be changed if your hosting service provider and your Registrar are from two different companies.
Hosting
IP (Internet Protocol Security) also abbreviated as (IPSec). However, IPSec is a network protocol that encrypts and authenticates the packets of data that is sent over a network. In addition, IPsec also includes the protocols to establish mutual authentication between the agents at the beginning of the session and negotiation of cryptographic keys to use during the session. IPSec can also protect the data flows between security gateways and hosts, it uses cryptographic security to protect communications over Internet protocol network. (Technet.microsoft, 2018)

Registras
IP (Internet Protocol Security) also abbreviated as (IPSec). However, IPSec is a network protocol that encrypts and authenticates the packets of data that is sent over a network. In addition, IPsec also includes the protocols to establish mutual authentication between the agents at the beginning of the session and negotiation of cryptographic keys to use during the session. IPSec can also protect the data flows between security gateways and hosts, it uses cryptographic security to protect communications over Internet protocol network. (Technet.microsoft, 2018)
Domains
IP (Internet Protocol Security) also abbreviated as (IPSec). However, IPSec is a network protocol that encrypts and authenticates the packets of data that is sent over a network. In addition, IPsec also includes the protocols to establish mutual authentication between the agents at the beginning of the session and negotiation of cryptographic keys to use during the session. IPSec can also protect the data flows between security gateways and hosts, it uses cryptographic security to protect communications over Internet protocol network. (Technet.microsoft, 2018)
Network Toplogies:
Bus
Bus is when there is a single cable and all the devices are connected to it. Therefore, this is easy to install, the disadvantage of this connection is that if one link breaks then everyone connected will be effected.(Messer, 2018)

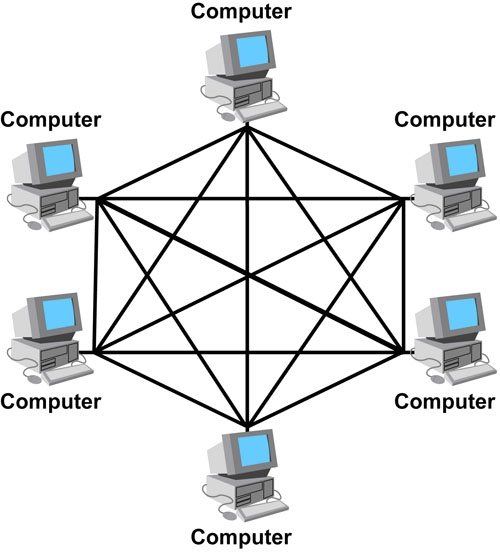
Mesh
A network with a mesh topology. However, Mesh has one or more connections to multiple sites. In addition, there is fully meshed networks where every website is connected to every other site. Partially meshed networks also has some sites with multiple connections but not to every other location. Thus, this is good to avoid uptime problems and load balancing. In addition, Mesh is usually used in WANs, which stands for “Wide Area Networks”(Messer, 2018)
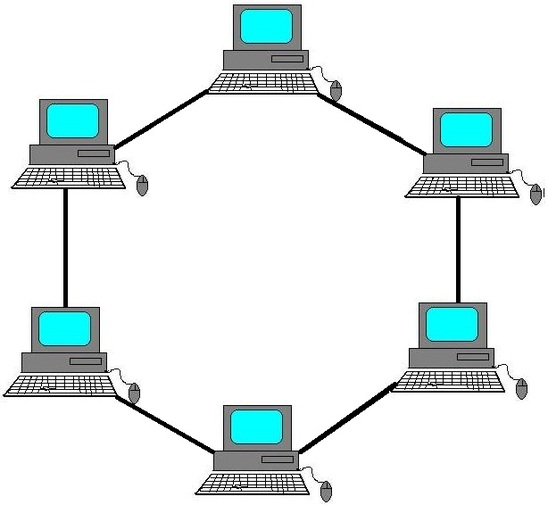
Ring
Ring is used for MANs, which is referred to as "Metro Area Networks" and WANs "Wide Area Networks", Rings send the same information from both sides of the Ring, which is good in case any break happens then the information will be delivered from the other way.(Messer, 2018)
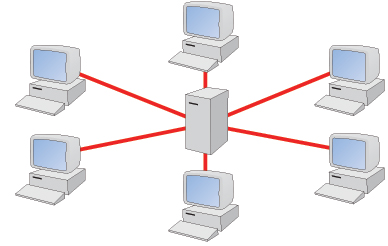
Star
Star topology is used in small and large networks, where there is a central device in the middle and all the devices are connected to it.(Messer, 2018)
Hybrid
Hybrid is a combination of one or more topologies.(Messer, 2018)