
IP Security
IP (Internet Protocol Security) also abbreviated as (IPSec). However, IPSec is a network protocol that encrypts and authenticates the packets of data that is sent over a network. In addition, IPsec also includes the protocols to establish mutual authentication between the agents at the beginning of the session and negotiation of cryptographic keys to use during the session. IPSec can also protect the data flows between security gateways and hosts, it uses cryptographic security to protect communications over Internet protocol network. (Technet.microsoft, 2018)
Public Key Infrastructure / Certification Authorities
Public Key Infrastructure also abbreviated as (PKI). PKI is a set of policies, procedures, roles, use, distribute, store and revoke digital certificates and manage public-key encryption. However, the purpose of PKI to securely transfer information for a range of network activities such as internet banking. (En.wikipedia, 2018) Certification Authority also abbreviated as (CA), CA issues digital certificates, a certificate that shows ownership of a public key by the names subject of the certificate.(En.wikipedia, 2018)
SSH (Secure Shell)
SSH stands for Secure Shell, SSH enables file transfers over unsecured networks and it enables secure system administration. SSH is used in large enterprises and in data centres. In addition, it uses port 22 and it uses an encryption to establish a secure connection between a server and a client. Everything gets encrypted files transfers, commands, and output and user authentication to protect the network from attackers.(Secure Shell, 2018)
Authentication
Authentication is the process where an individual is defined based on the username and password. However, authentication ensures that the individual is who she or he claims to be. In addition, authentication is used by servers, so the server knows who is trying to gain access to their site or information. (Webopedia, 2018)
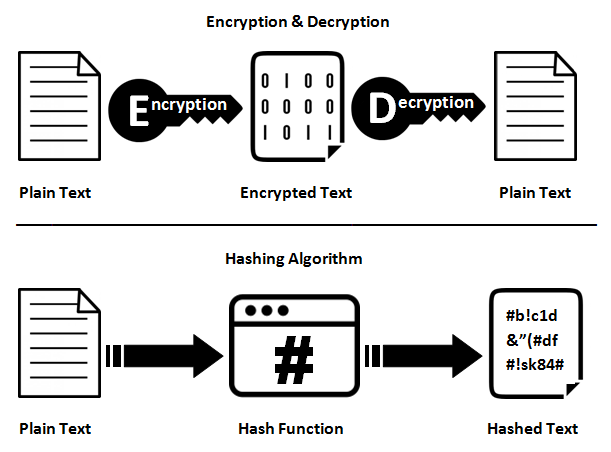
Encryption
Encryption is the process of transforming some data so that the encryption becomes unreadable by anyone unless the person has the decryption key. In addition, Encryption makes it more safe for people to send credit card numbers, security numbers, and home addresses over the internet without running the risk of being intercepted during the transit.(Anon, 2018)

Data Hashing
Data Hashing is when a string of characters are transformed into a key or a shorter fixed-length value, which represents the original string. However, hashing is used to index and retrieve items in a database because it is faster to find items using a shorter hashed key than using the original value. It is also used in many encryption algorithms.(SearchSQLServer, 2018)
PKI - Non- Repudiation
PKI stands for (Public Key Infrastructure), PKI enables integration of services related to cryptography. In addition, the goal of PKI is to provide access control, non-repudiation, authentication and integrity.
Non-repudiation is a process of ensuring that the receiver or the sender of a specific message can't deny either sending or receiving that specific message in the future. However, in non-repudiation one of the most important audit checks is a time stamp.
PKI has three primary functions:
-Digital signature, Encryption, decryption and key exchange.
Every user will have two keys in PKI, those keys are also known as "pair of keys". One of the keys is called the private key and the second key in the public key. However, the private key pretty much explains itself it’s a key that is kept with the owner and never revealed, and the public key is accessible by everyone and its stored on the key repository. Those keys are used to encrypt and decrypt messages. (Packtpub, 2018)
RADIUS (Remote Authentication Dial in User Service)
RADIUS is a client/server protocol that establishes a communication by enabling the remote access servers to communicate with a central server to authenticate dial-in users and authorize their access to the service. Due to RADIUS companies can maintain user profiles in a database that remote servers can share. (SearchSecurity, 2018)
TACAS (Terminal Access Controller Access Control System)
TACAS is an authentication protocol, TACAS allows the remote access server to send the users logins to the authentication server, which determines if the user should be given the access to the system or not. (SearchSecurity, 2018)
CHAP (Challenge Handshake Authentication Protocol)
CHAP protects users against replay attacks. CHAP requires both the server and the client even though it is not send over the network. However, it provides more security compared PAP (Password Authentication Protocol) (En.wikipedia, 2018)
EAP (Extensible Authentication Protocol)
EAP is a protocol for networks, EAP expans authentication methods used by PPP, which stands for (Point-to-Point Protocol), which is a protocol used when connecting a PC to the internet. In addition, EAP supports many authentication mechanisms, such as smart cards, one-time passwords, certificates and token cards. (SearchSecurity, 2018)
IPS and IDS
Both IPS and IDS increases the security of networks,IPS stands for (Intrusion Detection System) and IDS stands for (Intrusion Detection System), where they both insepct and monitor traffic, scan for suspicious data. In addition, detection in both IDS and IPS are based on signatures thats already recognized. The difference between IPS and IDS is how they treat the attacks. IPS controls the access to the networks in order to protect the system from attacks. IPS inspects the attack data and blocks it. IDS provides the network with preventive security against any suspicious activity. This is achieved through warnings aimed to the systems administrator but IDS is not designed to block attacks.(Pandasecurity, 2018)
Vulnerability Scanners
Vulnerability Scanner is a program used to scan applications, networks or systems for weaknesses. Where then hackers for example can abuse those weaknesses and gain access to the system and steal data. In addition, there is two types on scans, authenticated scans, which allows scanners to directly access netowrks and unauthenticated scans, is the second method and it results in high number of false positives and it is uncapable of providing detailed information
Capturing Methods
Many methods are available to capture unstructerd data from documents(forms, fax, email, letters, invoices). Some methods used for capturing are: manual keying, nearshore keying, single click, Intelligent character recognition, bar code recognition ... (ProcessFlows, 2018)